- Nikto for Windows with some extra features. Contribute to sensepost/wikto development by creating an account on GitHub. Nikto for Windows with some extra features. Contribute to sensepost/wikto development by creating an account on GitHub. Download ZIP Launching GitHub Desktop. If nothing happens, download GitHub Desktop and try again.
- Download abus for windows for free. Internet & Network tools downloads - ABUS IP-Installer by ABUS Security-Center GmbH & Co. KG and many more programs are available for instant and free download.
Nikto Download For Windows 10
In the past we learned how to use Nmap, Nessus and OpenVAS to look for vulnerabilities. This time we'll explore Nikto, a vulnerabilities scanner written in Perl, to check for Web Application vulnerabilities and footprinting (getting useful information about the target).
Installing Nikto:
In this case I'm using a Debian system, you can download Nikto for Debian at https://packages.debian.org/jessie/all/nikto/download . In case your system returns dependency errors when executing 'dpkg -i ' (as explained at https://linuxhint.com/uninstall-debian-packages/) execute the command 'apt –fix-broken install' and you'll get it installed.
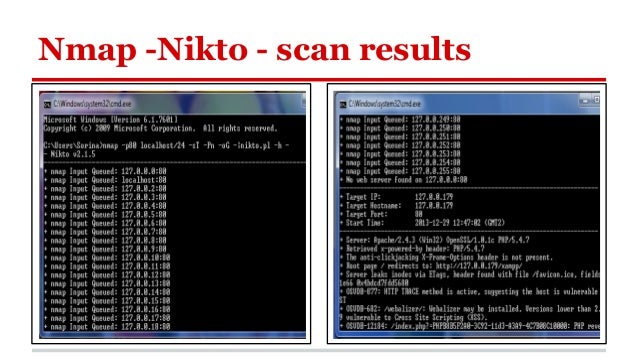
Operating system Windows 7, 64 bit Steps Nikto Version 2.1.5 Download and install Nikto and Nmap, Put in the Environment Variables, Path for the two folders of the programs mentioned above, In Start search for cmd, wait to open Command Prompt, Type the following for localhost, port 80: nmap -p80 localhost/24 -sT -Pn -oG - nikto.pl -h - Nmap. Download Nikto For Windows 10 Mount And Blade Gekokujo Guide Core De Force Nutrition Guide Pdf Ibm Iseries Business Partners Eeepc Sci Raid Host Controller Google Play Services Para Android 4.1.2 Male Body Mods Skyrim Download Motogp. Download Nessus and Nessus Manager. Tenable GPG Key (Red Hat ES 6 / CentOS 6 / Oracle Linux 6 (including Unbreakable Enterprise Kernel).
Getting started with Nikto:
Like with any Linux package you can always throw a 'man nikto' to learn all parameters. The first parameter we'll use, and which is mandatory, is -host (or -h)to specify the target. In this case I decided to use as target a very old unmaintained website which may throw interesting results:
As with any scanner we receive basic information useful in a footprinting process but additionally we can see within the first results Nikto already discovered a possible vulnerability exposing the website to Clickjacking attacks.
After seeing Nikto's recommendation to add the '-C all' parameter, I stopped the scanning, you can restart including -C all.
CGI (Common Gateway Interface) is a way through which Web Servers interact with software or programs installed on the server.
In this case we weren't lucky but as shown above, Nikto successfully found a possible vulnerability despite the website has not CGI content, take in consideration vulnerabilities may be false positive therefore not exploitable.
Let's check a different target, www.telered.com.ar , an Internet provider website:
The website has no redirection to www so I launched the scan again.
You can see they are using an old Apache version under CentOS and several possible vulnerabilities like OSVDB-877, OSVDB-3092, OSVDB-3268, OSVDB-3233, in the past we could search in the http://www.osvdb.org database but it is offline now, therefore we'll need to base the vulnerability on the information Nikto provides or to google it, in this case we would google Cross Site Tracing attacks.
Let's combine Nikto with Nmap, so we can see what ports a Webserver has open before using Nikto, ill throw a basic Nmap scan against the same target to check if it has additional ports open.
The interesting here may be the port 5060 used for VOIP, the port seems associated with known vulnerabilities according to this source, through Nikto it is unlikely to give important results but let's try it.
Where
-p = specifies the port. Uptodown games free download.
-h = specifies the host
-useproxy = to scan using a proxy and avoid the target to see our IP.
In contrast with the scan we launched before now Nikto found a XML file linking us to a blog article explaining the vulnerability the file may represent. It is recommendable to run Nmap against a target before using Nikto to target open ports.
It is important to highlight Nikto results will differ according to the parameters and data we use, even against the same target, for example, if you use the target's domain name or the target's IP or change the port. Let's see if we can find a third different result on the same target:
The result is very similar in this case, despite more errors were reported (21 vs 18 the first scan), possibly due redirection issues.
Multiple port scanning with Nikto:
If we run Nmap to discover a site has multiple ports open we can scan all them in a single Nikto session by separating ports with coma as shown below:
I run:
As you see after getting all open ports by Nmap I threw a Nikto scan, it automatically discards ports which are not running web applications. By adding all ports Nikto discovered multiple vulnerabilities including very sensitive directories holding possible credentials, SQL Injection and XSS vulnerabilities, brute force possibilities among a lot more of opportunities to exploit the server.
To reproduce Nikto results with complete results just run:
Using Nikto plugins:
'Nikto -list-plugins' will display a list of additional plugins which may help to scan a target or confirm a vulnerability reported by Nikto.
Let's verify if the results above showing XSS vulnerabilities are not a false positive.
Run:
Download Nikto For Windows Xp
As we see in this case Nikto informs '‘message' => ‘Expectation Failed' discarding the XSS vulnerability, if it was your server you could use different plugins to discard or confirm the rest of vulnerabilities.
Conclusion:
Nikto is a very light vulnerabilities scanner for web servers, it is useful if you have no time to deal with heavy scanners like Nexpose or Nessus, despite this, if you have time to analyze your target I would recommend a more complete scanner like Nexpose, Nessus, OpenVAS or Nmap, some of which we already analyzed at LinuxHint simply because they are not limited to web servers and all aspects deserve to be deeply checked in order to protect a server.
Download Autopsy
Version 4.17.0 for Windows
Download for Linux and OS X
Autopsy 4 will run on Linux and OS X. To do so:
- Download the Autopsy ZIP file
- Linux will need The Sleuth Kit Java .deb Debian package
- Follow the instructions to install other dependencies
3rd Party Modules
3rd party add-on modules can be found in the Module github repository.
From this repository, you can download all modules or just the ones that you want.
Utorrent download speed very slow mac. A short tutorial on how to fix the slow download speed of uTorrent.Wallpaper from this video:a comment if. Increase uTorrent download speed by tweaking uTorrent Setting. Optimized uTorrent can give you. Switch to a Different Website. If a website has set download speed limits on their end, or if their.
Older Versions
You can find other versions of Autopsy at:

- Nikto for Windows with some extra features. Contribute to sensepost/wikto development by creating an account on GitHub. Nikto for Windows with some extra features. Contribute to sensepost/wikto development by creating an account on GitHub. Download ZIP Launching GitHub Desktop. If nothing happens, download GitHub Desktop and try again.
- Download abus for windows for free. Internet & Network tools downloads - ABUS IP-Installer by ABUS Security-Center GmbH & Co. KG and many more programs are available for instant and free download.
Nikto Download For Windows 10
In the past we learned how to use Nmap, Nessus and OpenVAS to look for vulnerabilities. This time we'll explore Nikto, a vulnerabilities scanner written in Perl, to check for Web Application vulnerabilities and footprinting (getting useful information about the target).Installing Nikto:
In this case I'm using a Debian system, you can download Nikto for Debian at https://packages.debian.org/jessie/all/nikto/download . In case your system returns dependency errors when executing 'dpkg -i ' (as explained at https://linuxhint.com/uninstall-debian-packages/) execute the command 'apt –fix-broken install' and you'll get it installed.
Operating system Windows 7, 64 bit Steps Nikto Version 2.1.5 Download and install Nikto and Nmap, Put in the Environment Variables, Path for the two folders of the programs mentioned above, In Start search for cmd, wait to open Command Prompt, Type the following for localhost, port 80: nmap -p80 localhost/24 -sT -Pn -oG - nikto.pl -h - Nmap. Download Nikto For Windows 10 Mount And Blade Gekokujo Guide Core De Force Nutrition Guide Pdf Ibm Iseries Business Partners Eeepc Sci Raid Host Controller Google Play Services Para Android 4.1.2 Male Body Mods Skyrim Download Motogp. Download Nessus and Nessus Manager. Tenable GPG Key (Red Hat ES 6 / CentOS 6 / Oracle Linux 6 (including Unbreakable Enterprise Kernel).
Getting started with Nikto:
Like with any Linux package you can always throw a 'man nikto' to learn all parameters. The first parameter we'll use, and which is mandatory, is -host (or -h)to specify the target. In this case I decided to use as target a very old unmaintained website which may throw interesting results:
As with any scanner we receive basic information useful in a footprinting process but additionally we can see within the first results Nikto already discovered a possible vulnerability exposing the website to Clickjacking attacks.
After seeing Nikto's recommendation to add the '-C all' parameter, I stopped the scanning, you can restart including -C all.
CGI (Common Gateway Interface) is a way through which Web Servers interact with software or programs installed on the server.
In this case we weren't lucky but as shown above, Nikto successfully found a possible vulnerability despite the website has not CGI content, take in consideration vulnerabilities may be false positive therefore not exploitable.
Let's check a different target, www.telered.com.ar , an Internet provider website:
The website has no redirection to www so I launched the scan again.
You can see they are using an old Apache version under CentOS and several possible vulnerabilities like OSVDB-877, OSVDB-3092, OSVDB-3268, OSVDB-3233, in the past we could search in the http://www.osvdb.org database but it is offline now, therefore we'll need to base the vulnerability on the information Nikto provides or to google it, in this case we would google Cross Site Tracing attacks.
Let's combine Nikto with Nmap, so we can see what ports a Webserver has open before using Nikto, ill throw a basic Nmap scan against the same target to check if it has additional ports open.
The interesting here may be the port 5060 used for VOIP, the port seems associated with known vulnerabilities according to this source, through Nikto it is unlikely to give important results but let's try it.
Where
-p = specifies the port. Uptodown games free download.
-h = specifies the host
-useproxy = to scan using a proxy and avoid the target to see our IP.
In contrast with the scan we launched before now Nikto found a XML file linking us to a blog article explaining the vulnerability the file may represent. It is recommendable to run Nmap against a target before using Nikto to target open ports.
It is important to highlight Nikto results will differ according to the parameters and data we use, even against the same target, for example, if you use the target's domain name or the target's IP or change the port. Let's see if we can find a third different result on the same target:
The result is very similar in this case, despite more errors were reported (21 vs 18 the first scan), possibly due redirection issues.
Multiple port scanning with Nikto:
If we run Nmap to discover a site has multiple ports open we can scan all them in a single Nikto session by separating ports with coma as shown below:
I run:
As you see after getting all open ports by Nmap I threw a Nikto scan, it automatically discards ports which are not running web applications. By adding all ports Nikto discovered multiple vulnerabilities including very sensitive directories holding possible credentials, SQL Injection and XSS vulnerabilities, brute force possibilities among a lot more of opportunities to exploit the server.
To reproduce Nikto results with complete results just run:
Using Nikto plugins:
'Nikto -list-plugins' will display a list of additional plugins which may help to scan a target or confirm a vulnerability reported by Nikto.
Let's verify if the results above showing XSS vulnerabilities are not a false positive.
Run:
Download Nikto For Windows Xp
As we see in this case Nikto informs '‘message' => ‘Expectation Failed' discarding the XSS vulnerability, if it was your server you could use different plugins to discard or confirm the rest of vulnerabilities.
Conclusion:
Nikto is a very light vulnerabilities scanner for web servers, it is useful if you have no time to deal with heavy scanners like Nexpose or Nessus, despite this, if you have time to analyze your target I would recommend a more complete scanner like Nexpose, Nessus, OpenVAS or Nmap, some of which we already analyzed at LinuxHint simply because they are not limited to web servers and all aspects deserve to be deeply checked in order to protect a server.
Download Autopsy
Version 4.17.0 for Windows
Download for Linux and OS X
Autopsy 4 will run on Linux and OS X. To do so:
- Download the Autopsy ZIP file
- Linux will need The Sleuth Kit Java .deb Debian package
- Follow the instructions to install other dependencies
3rd Party Modules
3rd party add-on modules can be found in the Module github repository.
From this repository, you can download all modules or just the ones that you want.
Utorrent download speed very slow mac. A short tutorial on how to fix the slow download speed of uTorrent.Wallpaper from this video:a comment if. Increase uTorrent download speed by tweaking uTorrent Setting. Optimized uTorrent can give you. Switch to a Different Website. If a website has set download speed limits on their end, or if their.
Older Versions
You can find other versions of Autopsy at:
- Autopsy 4.4.0 and later: GitHub
- Autopsy 4.3.0 and earlier: Source Forge
Advanced
Six files are made available with each release:
- autopsy-X.X.X-32bit.msi: A 32-bit Windows installer.
- autopsy-X.X.X-64bit.msi: A 64-bit Windows installer.
- autopsy-X.X.X.zip: Used for Linux and OS X installations and for module developers.
- One .asc file (GPG signature) for each of the above files.
- Source code at github.com
- Brian's GPG Key: local copy or MIT's server
- See the Developer's Guide for details on the source code repository.
Bugs
See the support page for details on reporting bugs.
Announcements
Announcements of new releases are sent to the sleuthkit-announce and sleuthkit-users email lists and the RSS feed .
Download and Register
Version 4.17.0 for Windows
Cyber Triage is fast and affordable incident response software any organization can use to rapidly investigate its endpoints. Built by Brian Carrier, Cyber Triage is designed to support the needs of cyber first responders in law enforcement, consulting firms, and internal security teams. Basis Technology builds proven AI solutions for analyzing text, connecting data silos, & discovering digital evidence.
Brought to you by Cyber Triage & Basis Technology